These hacking Linux distros are armed with all the tools that you need to get started with penetration testing.

Apr 01, 2016 · Instead of simply methodology or process, PTES also provides hands-on technical guidelines for what/how to test, rationale of testing and recommended testing tools and usage. Payment Card Industry Data Security Standard (PCI DSS) Requirement 11.3 defines the penetration testing. PCI also defines

Aug 05, 2014 · This article is part of the new OWASP Testing Guide v4. Back to the OWASP Testing Guide v4 ToC: https://www.owasp.org/index.php/OWASP_Testing_Guide_v4_Table_of_Contents Back to the OWASP Testing Guide Project: https://www.owasp.org/index.php/OWASP_Testing…
Penetration Testing Services Get a real-world look at how attackers could exploit your vulnerabilities—and guidance on how to stop them—with our pen testing services.



Security mailing list archive for the Nmap lists, Bugtraq, Full Disclosure, Security Basics, Pen-test, and dozens more. Search capabilities and RSS feeds with smart excerpts are available

Learn penetration testing strategies, ethical hacking techniques to help security professionals evaluate the effectiveness of information security …
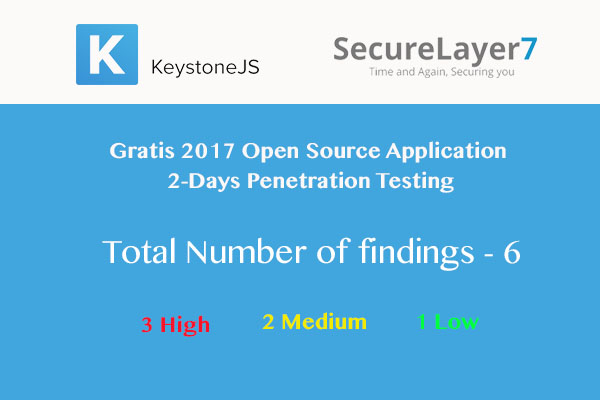
Learn the two major differences between proprietary tools and open source tools for software security testing.
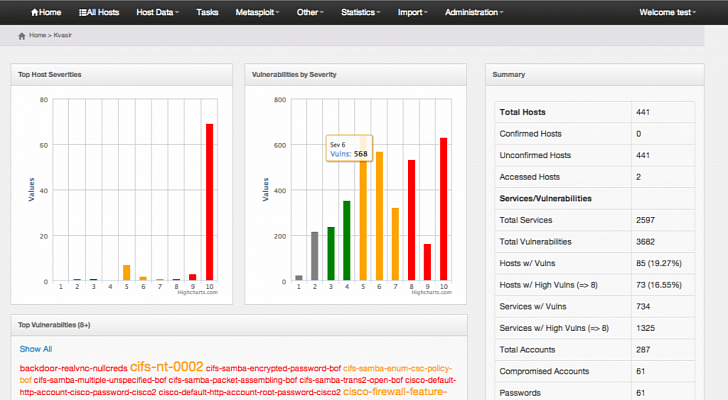
A collection of awesome penetration testing resources, tools and other shiny things

Fact does not come from the grand leaps of discovery but rather from the small, careful steps of verification. That is the premise of the Open Source Security Testing Methodology Manual also known as the OSSTMM (pronounced as “awstem”) It is a peer-reviewed manual of security testing and analysis which result in verified facts.
Home of Kali Linux, an Advanced Penetration Testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.